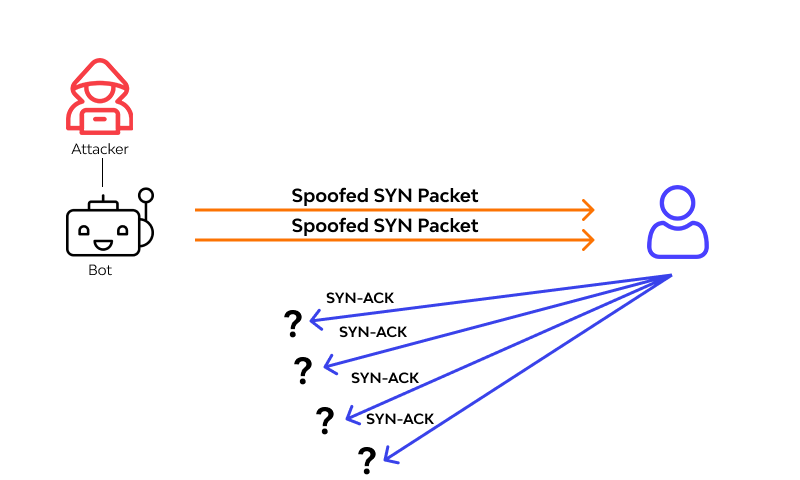
How to Manipulate a Cellphone Connection via TCP Manipulating a cellphone connection using the Transmission Control Protocol (TCP) involves
-
-
How Easily Can TikTok Be Hacked: A Full Exploitation Analysis TikTok, the global social media giant, boasts over a billion monthly active users
-
Educational Article: Understanding Instagram’s Security Features and How Ethical Hackers Analyze Them Instagram, with over 2 billion monthly active
-
Apple’s iOS is renowned for its robust security architecture, designed to protect user data and ensure device integrity. Understanding how iOS
-
Mastering secure device interactions is essential for protecting networks and systems. This educational article outlines how to ethically establish a
-
Exclusively for Hire a Hacker Pro and Hacker University The 900 MHz frequency band (902–928 MHz), part of the U.S. Industrial, Scientific, and
-
Accessing Home Cameras Remotely: A Technical Guide for Educational Purposes At Hacker University (https://hireahacker.pro), we empower students to
-
Disclaimer: This article is for educational purposes only, intended to inform aspiring hackers and cybersecurity professionals about mobile
-
Disclaimer: This article is for educational purposes only, aimed at cybersecurity researchers and ethical hackers. Engaging in black hat hacking is
-
How to Overcome 2FA on iPhone: A Technical Guide for Cybersecurity Professionals Disclaimer: This content is strictly for educational purposes,